Difference between revisions of "Personal Firewall"
CrazyGolem (Talk | contribs) (Created page with "Fixme network is not firewalled. If you connect to ''FIXME'' or ''FIXME-5GHz'' WiFi networks, you'll get a public IP address and your machine will be exposed to Internet. If you ...") |
(Added mac instructions) |
||
| (7 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Fixme network is not firewalled. If you connect to ''FIXME | + | Fixme network is not firewalled neither is NATed. If you connect to ''FIXME'' WiFi network, *you'll get a public IP address and your machine will be exposed to Internet*. If you connect to ''FIXME_NAT'', you won't have a public address, but it is however good practice to install a firewall. ''Remember that you are in a hackerspace, and that in hackerspaces there are hackers. Not protecting your machine is an invitation to the Lulz.'' |
== Linux == | == Linux == | ||
| − | You can use [https://help.ubuntu.com/community/UFW UFW • Uncomplicated Firewall], the default firewall configuration tool for Ubuntu ( | + | You can use [https://help.ubuntu.com/community/UFW UFW • Uncomplicated Firewall], the default firewall configuration tool for Ubuntu (disabled by default on Ubuntu). [http://gufw.tuxfamily.org GUFW] is a very nice and simple GUI for ufw. |
If you chose GUFW, you have to click on the ''Unlock'' button after starting the GUI, then check ''Activate'' or push the ''Status'' slider to the ''On'' position. The default configuration (Incoming: Deny; Outgoing: Allow) is a good start for beginners, and contrary to what it claims, critical service messages will still be able to reach your machine, as well as incoming packets for which you established the connexion (it is a stateful firewall). | If you chose GUFW, you have to click on the ''Unlock'' button after starting the GUI, then check ''Activate'' or push the ''Status'' slider to the ''On'' position. The default configuration (Incoming: Deny; Outgoing: Allow) is a good start for beginners, and contrary to what it claims, critical service messages will still be able to reach your machine, as well as incoming packets for which you established the connexion (it is a stateful firewall). | ||
| − | You can use <code>iptables -L</code> to list enforced rules. | + | You can use <code>sudo iptables -L</code> to list enforced rules. |
| − | Use <code>netstat -laputen | grep -i listen</code> to know which services are listening on which interface/port. If you activated the firewall, listening ports might not be reachable unless you configured your firewall to accept incoming connection to these services. | + | Use <code>netstat -laputen | grep -i listen</code> or <code>sudo lsof -i -n</code> to know which services are listening on which interface/port. If you activated the firewall, listening ports might not be reachable unless you configured your firewall to accept incoming connection to these services. |
| + | |||
| + | An alternative to the above use of ''netstat'' is <code>lsof -i -n</code> which shows open ports and open connections in a nice way. | ||
You can use ''nmap'' from another computer to determine whether there still are open ports on your machine after the firewall is configured: | You can use ''nmap'' from another computer to determine whether there still are open ports on your machine after the firewall is configured: | ||
| Line 17: | Line 19: | ||
Since Windows XP, a firewall is included in Windows. However, until Windows XP SP2 it was disabled by default. An unconfigured Windows Firewall denies inbound connections and allows outbound connections. | Since Windows XP, a firewall is included in Windows. However, until Windows XP SP2 it was disabled by default. An unconfigured Windows Firewall denies inbound connections and allows outbound connections. | ||
| − | There are more complete and free (i.e. gratis) solutions. You can find some of | + | There are more complete and free (i.e. gratis) solutions. You can find some of them on a [http://lifehacker.com/5061933/five-best-windows-firewalls rather old article of Lifehacker] or on Google. |
| + | |||
| + | Use <code>nmap</code> from another machine to test your firewall configuration. | ||
| + | |||
| + | == Mac == | ||
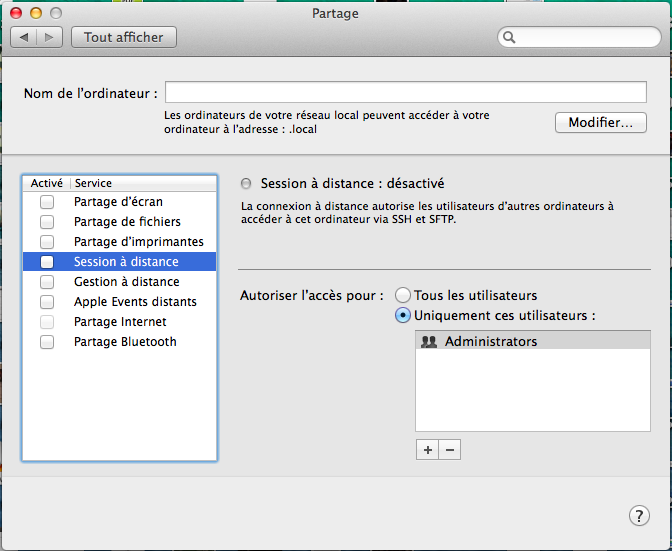
| + | Just deselect all sharing options. Unless you have any services you ran yourself (e.g. background tool, itunes sync, something over the command line, etc), this should cover most of what you need. | ||
| + | [[File:Mac_firewall.png]] | ||
Latest revision as of 17:25, 15 March 2015
Fixme network is not firewalled neither is NATed. If you connect to FIXME WiFi network, *you'll get a public IP address and your machine will be exposed to Internet*. If you connect to FIXME_NAT, you won't have a public address, but it is however good practice to install a firewall. Remember that you are in a hackerspace, and that in hackerspaces there are hackers. Not protecting your machine is an invitation to the Lulz.
Linux
You can use UFW • Uncomplicated Firewall, the default firewall configuration tool for Ubuntu (disabled by default on Ubuntu). GUFW is a very nice and simple GUI for ufw.
If you chose GUFW, you have to click on the Unlock button after starting the GUI, then check Activate or push the Status slider to the On position. The default configuration (Incoming: Deny; Outgoing: Allow) is a good start for beginners, and contrary to what it claims, critical service messages will still be able to reach your machine, as well as incoming packets for which you established the connexion (it is a stateful firewall).
You can use sudo iptables -L to list enforced rules.
Use netstat -laputen | grep -i listen or sudo lsof -i -n to know which services are listening on which interface/port. If you activated the firewall, listening ports might not be reachable unless you configured your firewall to accept incoming connection to these services.
An alternative to the above use of netstat is lsof -i -n which shows open ports and open connections in a nice way.
You can use nmap from another computer to determine whether there still are open ports on your machine after the firewall is configured:
-
nmap -sS <IP Address>will scan the specified IP Address for low-range ports (<1024). -
nmap -p- <IP Address>will scan all the ports of the machine behind the given IP Address.
Windows
Since Windows XP, a firewall is included in Windows. However, until Windows XP SP2 it was disabled by default. An unconfigured Windows Firewall denies inbound connections and allows outbound connections.
There are more complete and free (i.e. gratis) solutions. You can find some of them on a rather old article of Lifehacker or on Google.
Use nmap from another machine to test your firewall configuration.
Mac
Just deselect all sharing options. Unless you have any services you ran yourself (e.g. background tool, itunes sync, something over the command line, etc), this should cover most of what you need.