Difference between revisions of "RwthCTF 2011"
m (Created page with "= First Contact = <pre> Hi rwthCTF Teams, with this message, the first ever rwthCTF is officially in the "team-preparation" phase. Attached to this mail you can find the first i...") |
|||
| (17 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | [[Category:CTF]] | |
<pre> | <pre> | ||
| + | HTTP/1.1 301 Moved Permanently | ||
| + | Location: http://hackerspace.fixme.ch/mediawiki/index.php/RwthCTF_2011 | ||
| + | </pre> | ||
| + | |||
| + | = Quick links = | ||
| + | |||
| + | * [https://grid.nimag.net/uri/URI%3ADIR2-RO%3Apn4ojukzl5wbr5qw7fumxzrlie%3Aobmcas6ttnjysvyahijofo2cumdsripjhkmqfczjxek2mvd3kghq/ Fichiers (network dumps, vm images, etc.)] | ||
| + | * [http://10.11.0.1/#scoreboard Scoreboard] | ||
| + | * [http://10.11.20.51/zabbix/index.php Monitoring] admin/zabbix | ||
| + | * [[Game]] | ||
| + | * [[Challenges]] | ||
| + | * Secret: shohwuinikeiquop | ||
| + | * Flag regex: <pre>^[a-zA-Z0-9]{40}$</pre> | ||
| + | |||
| + | = SSH Access = | ||
| + | |||
| + | Public key: | ||
| + | |||
| + | <pre> | ||
| + | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC5twrX47WdsuPX8BohNmuInE3Vjbd9XQ05gLMCjDaFaZDgt7B4BpQNfyGlvlCq3upPOwmpvFkH9+i7jSb3NCngN358OORWAuKm3rwLh0r1N/zL/uhz3Dzlpv1IFkm3Iev+J1eV1w4wfKhxvw2RyqL6t4csfowYlntpif5CCQ6wZqzJd+xFeJcTDlUHi9eVD8ew8qh4Wa2fZ1J4AdoKiYsVxHgVu2CzHGVKYSr217WuAiEg+P2guT/E99ZB4nRTWv8TNf4925BzsImvswNTnQjgh7h+q+zru4DncZn5EKlRJP/npTBcoLD274rLpehDdiBBKsIGNrwqYxWIi982ilPD FIXME@rwthCTF2011 | ||
| + | </pre> | ||
| + | |||
| + | '''Ask info@fixme.ch for the private key!''' | ||
| + | |||
| + | = Shared Git Repository = | ||
| + | |||
| + | <pre> | ||
| + | git clone fixme@guest1.fixme.ch:/home/fixme/rwthctf2011/repo/ rwthCTF-2011 | ||
| + | </pre> | ||
| + | |||
| + | Fancy tools, mass exploitation! | ||
| + | |||
| + | <pre> | ||
| + | $ scoreboard.py targets | foreach.py attack1.py | upload-flags.py | ||
| + | Hello Team FIXME! You may now submit flags, one per line. | ||
| + | 66c69cb0354079a1ad26e405851bc13c70964d51 | ||
| + | Unknown flag. | ||
| + | 5b713c95c31555bb76f8e4795e8a726c289918ce | ||
| + | Unknown flag. | ||
| + | [...] | ||
| + | </pre> | ||
| + | |||
| + | = First Contact = | ||
| + | |||
| + | '''Email''' | ||
| + | |||
| + | <div style="background-color: #eee; padding:3px; border: 1px dotted black"> | ||
Hi rwthCTF Teams, | Hi rwthCTF Teams, | ||
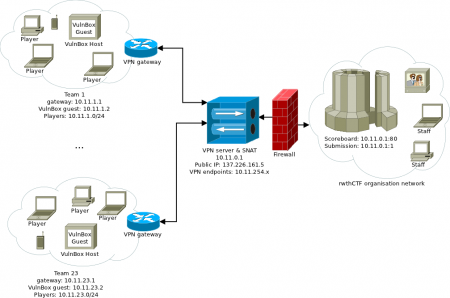
| − | with this message, the first ever rwthCTF is officially in the "team-preparation" phase. Attached to this mail you can find the first instructional README.txt file, a rough diagram of our | + | with this message, the first ever rwthCTF is officially in the "team-preparation" phase. Attached to this mail you can find the first instructional README.txt file, a rough diagram of our network setup and a second document (codewars.txt) that serves as a small appetizer for the upcoming challenges in the CTF. The appetizer (codewars documentation) only describes a small part of the CTF event - we will have lots of programming languages and skill areas covered. Also the scripts mentioned in the document will only be made available when the competition starts. |
| − | + | ||
| − | + | ||
| − | Additionally we prepared a "test-vulnbox" that can be downloaded from the link below. This is _NOT_ the final vulnbox image. Please refer to the README for further pointers. You will need this | + | Additionally we prepared a "test-vulnbox" that can be downloaded from the link below. This is _NOT_ the final vulnbox image. Please refer to the README for further pointers. You will need this once VPN credentials are released - probably on next Monday (again see README). |
| − | + | ||
| − | This E-Mail is signed with a PGP key and sent in PGP/MIME. Please download the corresponding public key from http://ctf.itsec.rwth-aachen.de/ and verify the signature. All further mail | + | This E-Mail is signed with a PGP key and sent in PGP/MIME. Please download the corresponding public key from http://ctf.itsec.rwth-aachen.de/ and verify the signature. All further mail communication from rwthCTF organizers will be signed with this key as well. |
| − | + | ||
Cheers, | Cheers, | ||
| − | + | ||
| + | rwthCTF Orga | ||
Test-Vulnbox: xxxxxxx | Test-Vulnbox: xxxxxxx | ||
| + | |||
GPG-symmetric-passphrase: xxxxxxx | GPG-symmetric-passphrase: xxxxxxx | ||
| + | </div> | ||
| + | |||
| + | |||
| + | '''Attachments: ''' [[File:README.txt]] [[File:codewars.txt]] | ||
| + | |||
| + | [[File:network.png|450px]] | ||
| + | |||
| + | = VPN Credentials = | ||
| + | |||
| + | '''Email''' | ||
| + | |||
| + | <div style="background-color: #eee; padding:3px; border: 1px dotted black"> | ||
| + | Hi rwthCTF Teams, | ||
| + | |||
| + | with this mail you get your VPN credentials. This includes the openvpn config | ||
| + | file (client.conf), your team certificate (teamX.cert) and your private key | ||
| + | (teamX.key). Also needed by OpenVPN and attached to this mail are the CA | ||
| + | certificate "rwthctfca.pem" and a TLS shared key "ta.key". These credentials can | ||
| + | only be used from _ONE_ machine at a time. | ||
| + | |||
| + | The X in the files you receive is your team ID. This also specifies your IP | ||
| + | subnet 10.11.X.0/24! Please refer to the earlier README.txt for further details. | ||
| + | |||
| + | Please connect to the VPN, set your IP addresses and bring up your routing. Also | ||
| + | start the Test Vulnbox and set it to 10.11.X.2. | ||
| + | |||
| + | You can view a preliminary scoreboard at http://10.11.0.1/ During the CTF we | ||
| + | allow flag submission at 10.11.0.1 port 1/tcp. This should already be online for | ||
| + | testing purposes, but you can not score any points before the CTF starts on | ||
| + | September 30th. The rest of the network is pretty locked down at the moment - | ||
| + | you may ICMP, though. | ||
| + | |||
| + | Any further questions should be asked via E-Mail or the #rwthctf IRC channel on | ||
| + | freenode. | ||
| + | |||
| + | One last thing: each team was assigned a unique secret passphrase (secret.txt) | ||
| + | that is needed for certain critical actions during the competition. Keep it | ||
| + | safe! | ||
| + | |||
| + | Cheers, | ||
| + | -rwthCTF Orga | ||
| + | </div> | ||
| + | |||
| + | = Thanks = | ||
| + | <div style="background-color: #eee; padding:3px; border: 1px dotted black"> | ||
| + | Hi rwthCTF Teams, | ||
| + | |||
| + | thank you for participating in the rwthCTF 2011 competition. Hopefully we will meet again at another event or next year at rwthCTF. | ||
| + | |||
| + | We updated the website with some pictures taken during the CTF and some results. Give it a visit at http://ctf.itsec.rwth-aachen.de/ | ||
| + | |||
| + | Thanks again, | ||
| + | -rwthCTF Orga | ||
| + | </div> | ||
| + | |||
| + | = Network = | ||
| + | |||
| + | * [[File:network-setup.pdf]] | ||
| + | * labo.ctrlaltdel.ch: Virtual machine host | ||
| + | * rwthctf.fixme.ch: OpenVPN router | ||
| + | |||
| + | '''10.11.20.0/25 DMZ''' | ||
| + | * 10.11.20.1 OpenVPN router | ||
| + | * 10.11.20.2 Vulnbox | ||
| + | * 10.11.20.3 Test vulnbox (dès le début de la compétition) | ||
| + | * 10.11.20.50 ructfe2010 vulnbox (testing purpose) | ||
| + | * 10.11.20.51 Monitoring | ||
| + | '''10.11.20.128/25 VPN clients''' | ||
| + | * 10.11.20.129 OpenVPN router | ||
| + | |||
| + | Une capture réseau (tcpdump) tourne en permanence et sauve le trafic à destination de la vulnbox depuis le réseau du concours. Un nouveau fichier est créé chaque heure (attention aux sessions TCP coupées). | ||
| + | |||
| + | === Tcpdump === | ||
| + | |||
| + | <pre> | ||
| + | ssh root@rwthctf.fixme.ch | ||
| + | root@openvpn:~# ls /srv/network-dumps/ | ||
| + | </pre> | ||
| + | |||
| + | === Snort === | ||
| + | |||
| + | How to update the Snort IPS rules? | ||
| + | |||
| + | <pre> | ||
| + | ssh root@rwthctf.fixme.ch | ||
| + | root@openvpn:~# vi /usr/local/etc/snort/rules/local.rules | ||
| + | root@openvpn:~# sv restart snort | ||
| + | </pre> | ||
| + | |||
| + | == Orga Network == | ||
| + | |||
| + | * 10.11.0.1 Scoreboard + Flag submission | ||
| + | * 10.11.199.1 Vidéo surveillance? | ||
| + | |||
| + | == Config OpenVPN == | ||
| + | |||
| + | * Créer un compte utilisateur après vous être connecté sur root@rwthctf.fixme.ch | ||
| + | * Créer les deux fichiers suivants | ||
| + | * ''$ openvpn openvpn.conf'' et entrer votre nom d'utilisateur/mot de passe | ||
| + | |||
| + | '''openvpn.conf''' | ||
| + | |||
| + | <pre> | ||
| + | client | ||
| + | remote rwthctf.fixme.ch | ||
| + | ca ./ca.pem | ||
| + | auth-user-pass | ||
| + | dev tun | ||
| + | proto tcp | ||
| + | nobind | ||
| + | persist-key | ||
| + | persist-tun | ||
| + | comp-lzo | ||
| + | </pre> | ||
| + | |||
| + | '''ca.pem''' | ||
| + | |||
| + | <pre> | ||
| + | -----BEGIN CERTIFICATE----- | ||
| + | XXX | ||
| + | -----END CERTIFICATE----- | ||
</pre> | </pre> | ||
Latest revision as of 09:14, 22 October 2012
HTTP/1.1 301 Moved Permanently Location: http://hackerspace.fixme.ch/mediawiki/index.php/RwthCTF_2011
Contents
Quick links
- Fichiers (network dumps, vm images, etc.)
- Scoreboard
- Monitoring admin/zabbix
- Game
- Challenges
- Secret: shohwuinikeiquop
- Flag regex:
^[a-zA-Z0-9]{40}$
SSH Access
Public key:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC5twrX47WdsuPX8BohNmuInE3Vjbd9XQ05gLMCjDaFaZDgt7B4BpQNfyGlvlCq3upPOwmpvFkH9+i7jSb3NCngN358OORWAuKm3rwLh0r1N/zL/uhz3Dzlpv1IFkm3Iev+J1eV1w4wfKhxvw2RyqL6t4csfowYlntpif5CCQ6wZqzJd+xFeJcTDlUHi9eVD8ew8qh4Wa2fZ1J4AdoKiYsVxHgVu2CzHGVKYSr217WuAiEg+P2guT/E99ZB4nRTWv8TNf4925BzsImvswNTnQjgh7h+q+zru4DncZn5EKlRJP/npTBcoLD274rLpehDdiBBKsIGNrwqYxWIi982ilPD FIXME@rwthCTF2011
Ask info@fixme.ch for the private key!
git clone fixme@guest1.fixme.ch:/home/fixme/rwthctf2011/repo/ rwthCTF-2011
Fancy tools, mass exploitation!
$ scoreboard.py targets | foreach.py attack1.py | upload-flags.py Hello Team FIXME! You may now submit flags, one per line. 66c69cb0354079a1ad26e405851bc13c70964d51 Unknown flag. 5b713c95c31555bb76f8e4795e8a726c289918ce Unknown flag. [...]
First Contact
Hi rwthCTF Teams,
with this message, the first ever rwthCTF is officially in the "team-preparation" phase. Attached to this mail you can find the first instructional README.txt file, a rough diagram of our network setup and a second document (codewars.txt) that serves as a small appetizer for the upcoming challenges in the CTF. The appetizer (codewars documentation) only describes a small part of the CTF event - we will have lots of programming languages and skill areas covered. Also the scripts mentioned in the document will only be made available when the competition starts.
Additionally we prepared a "test-vulnbox" that can be downloaded from the link below. This is _NOT_ the final vulnbox image. Please refer to the README for further pointers. You will need this once VPN credentials are released - probably on next Monday (again see README).
This E-Mail is signed with a PGP key and sent in PGP/MIME. Please download the corresponding public key from http://ctf.itsec.rwth-aachen.de/ and verify the signature. All further mail communication from rwthCTF organizers will be signed with this key as well.
Cheers,
rwthCTF Orga
Test-Vulnbox: xxxxxxx
GPG-symmetric-passphrase: xxxxxxx
Attachments: File:README.txt File:Codewars.txt
VPN Credentials
Hi rwthCTF Teams,
with this mail you get your VPN credentials. This includes the openvpn config file (client.conf), your team certificate (teamX.cert) and your private key (teamX.key). Also needed by OpenVPN and attached to this mail are the CA certificate "rwthctfca.pem" and a TLS shared key "ta.key". These credentials can only be used from _ONE_ machine at a time.
The X in the files you receive is your team ID. This also specifies your IP subnet 10.11.X.0/24! Please refer to the earlier README.txt for further details.
Please connect to the VPN, set your IP addresses and bring up your routing. Also start the Test Vulnbox and set it to 10.11.X.2.
You can view a preliminary scoreboard at http://10.11.0.1/ During the CTF we allow flag submission at 10.11.0.1 port 1/tcp. This should already be online for testing purposes, but you can not score any points before the CTF starts on September 30th. The rest of the network is pretty locked down at the moment - you may ICMP, though.
Any further questions should be asked via E-Mail or the #rwthctf IRC channel on freenode.
One last thing: each team was assigned a unique secret passphrase (secret.txt) that is needed for certain critical actions during the competition. Keep it safe!
Cheers, -rwthCTF Orga
Thanks
Hi rwthCTF Teams,
thank you for participating in the rwthCTF 2011 competition. Hopefully we will meet again at another event or next year at rwthCTF.
We updated the website with some pictures taken during the CTF and some results. Give it a visit at http://ctf.itsec.rwth-aachen.de/
Thanks again, -rwthCTF Orga
Network
- File:Network-setup.pdf
- labo.ctrlaltdel.ch: Virtual machine host
- rwthctf.fixme.ch: OpenVPN router
10.11.20.0/25 DMZ
- 10.11.20.1 OpenVPN router
- 10.11.20.2 Vulnbox
- 10.11.20.3 Test vulnbox (dès le début de la compétition)
- 10.11.20.50 ructfe2010 vulnbox (testing purpose)
- 10.11.20.51 Monitoring
10.11.20.128/25 VPN clients
- 10.11.20.129 OpenVPN router
Une capture réseau (tcpdump) tourne en permanence et sauve le trafic à destination de la vulnbox depuis le réseau du concours. Un nouveau fichier est créé chaque heure (attention aux sessions TCP coupées).
Tcpdump
ssh root@rwthctf.fixme.ch root@openvpn:~# ls /srv/network-dumps/
Snort
How to update the Snort IPS rules?
ssh root@rwthctf.fixme.ch root@openvpn:~# vi /usr/local/etc/snort/rules/local.rules root@openvpn:~# sv restart snort
Orga Network
- 10.11.0.1 Scoreboard + Flag submission
- 10.11.199.1 Vidéo surveillance?
Config OpenVPN
- Créer un compte utilisateur après vous être connecté sur root@rwthctf.fixme.ch
- Créer les deux fichiers suivants
- $ openvpn openvpn.conf et entrer votre nom d'utilisateur/mot de passe
openvpn.conf
client remote rwthctf.fixme.ch ca ./ca.pem auth-user-pass dev tun proto tcp nobind persist-key persist-tun comp-lzo
ca.pem
-----BEGIN CERTIFICATE----- XXX -----END CERTIFICATE-----