RwthCTF 2011
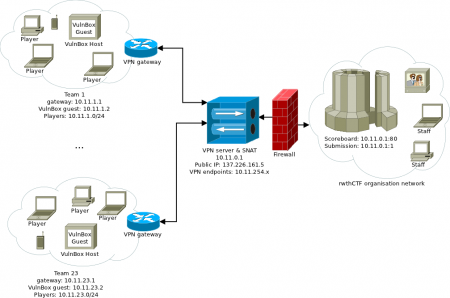
Our setup
- OpenVPN server 62.220.138.151
First Contact
Hi rwthCTF Teams,
with this message, the first ever rwthCTF is officially in the "team-preparation" phase. Attached to this mail you can find the first instructional README.txt file, a rough diagram of our network setup and a second document (codewars.txt) that serves as a small appetizer for the upcoming challenges in the CTF. The appetizer (codewars documentation) only describes a small part of the CTF event - we will have lots of programming languages and skill areas covered. Also the scripts mentioned in the document will only be made available when the competition starts.
Additionally we prepared a "test-vulnbox" that can be downloaded from the link below. This is _NOT_ the final vulnbox image. Please refer to the README for further pointers. You will need this once VPN credentials are released - probably on next Monday (again see README).
This E-Mail is signed with a PGP key and sent in PGP/MIME. Please download the corresponding public key from http://ctf.itsec.rwth-aachen.de/ and verify the signature. All further mail communication from rwthCTF organizers will be signed with this key as well.
Cheers,
rwthCTF Orga
Test-Vulnbox: xxxxxxx
GPG-symmetric-passphrase: xxxxxxx
Attachments: File:README.txt File:Codewars.txt