Difference between revisions of "OpenVPN"
From Fixme.ch
(→Command Line) |
|||
| (13 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Services]] | [[Category:Services]] | ||
== Information == | == Information == | ||
| − | * | + | * Easy access to the FIXME [[Network]] from the outside world |
| − | * | + | * This is part of the [[Internal_Server]] |
| + | * You must have a local account on foo and be in the '''vpnusers''' unix group | ||
| + | == Client configuration == | ||
| + | === Command Line === | ||
| + | * Copy this to ca.crt | ||
| + | <pre> | ||
| + | -----BEGIN CERTIFICATE----- | ||
| + | MIIDvDCCAyWgAwIBAgIJALowX2zad5mbMA0GCSqGSIb3DQEBBQUAMIGbMQswCQYD | ||
| + | VQQGEwJDSDELMAkGA1UECBMCVkQxETAPBgNVBAcTCExhdXNhbm5lMRowGAYDVQQK | ||
| + | ExFGSVhNRSBIQUNLRVJTUEFDRTEMMAoGA1UECxMDVlBOMRUwEwYDVQQDEwxmb28u | ||
| + | Zml4bWUuY2gxDjAMBgNVBCkTBUZJWE1FMRswGQYJKoZIhvcNAQkBFgx2cG5AZml4 | ||
| + | bWUuY2gwHhcNMTIxMjI4MjMzODE4WhcNMjIxMjI2MjMzODE4WjCBmzELMAkGA1UE | ||
| + | BhMCQ0gxCzAJBgNVBAgTAlZEMREwDwYDVQQHEwhMYXVzYW5uZTEaMBgGA1UEChMR | ||
| + | RklYTUUgSEFDS0VSU1BBQ0UxDDAKBgNVBAsTA1ZQTjEVMBMGA1UEAxMMZm9vLmZp | ||
| + | eG1lLmNoMQ4wDAYDVQQpEwVGSVhNRTEbMBkGCSqGSIb3DQEJARYMdnBuQGZpeG1l | ||
| + | LmNoMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDpL2ZXBJw9MX7b2iezP+P7 | ||
| + | +hI4XjXx1HCyV1TmM2sXCxenN+BmS9uD+hz/kOtHxakVHsm4QKkqcppNJGscpZis | ||
| + | HopK733rEviVARZxhn4ANEOp9JXeXu8hsy0hC5DEozGceSOzkxnJWUM64e7rhBzQ | ||
| + | CiZN7FDrJN2ok1ifFEojtQIDAQABo4IBBDCCAQAwHQYDVR0OBBYEFJV7oFA/wZX1 | ||
| + | Yp6enu/++UkotcrXMIHQBgNVHSMEgcgwgcWAFJV7oFA/wZX1Yp6enu/++UkotcrX | ||
| + | oYGhpIGeMIGbMQswCQYDVQQGEwJDSDELMAkGA1UECBMCVkQxETAPBgNVBAcTCExh | ||
| + | dXNhbm5lMRowGAYDVQQKExFGSVhNRSBIQUNLRVJTUEFDRTEMMAoGA1UECxMDVlBO | ||
| + | MRUwEwYDVQQDEwxmb28uZml4bWUuY2gxDjAMBgNVBCkTBUZJWE1FMRswGQYJKoZI | ||
| + | hvcNAQkBFgx2cG5AZml4bWUuY2iCCQC6MF9s2neZmzAMBgNVHRMEBTADAQH/MA0G | ||
| + | CSqGSIb3DQEBBQUAA4GBAAi2XgH93CxEhff2Q5tk/B2hzu+xtcBLzYjcgq1QqJ63 | ||
| + | ipG9maoav2UrjuWDjb+7WnzSe7JMF8Ay8CqWHgf9Dfqb04PLcIGPe5OPo8jlf4QF | ||
| + | k1uBZs0F+Z2v1yq4EK4KJ/hJxLJIX6xs5UGeK2GaaHKROuQX9N5iIb6BhyA5tlzd | ||
| + | -----END CERTIFICATE----- | ||
| + | </pre> | ||
| + | * Put the following content in a ''foo.cfg'' configuration file | ||
| + | <pre> | ||
| + | client | ||
| + | dev tun | ||
| + | proto udp | ||
| + | remote foo.fixme.ch 1194 | ||
| + | resolv-retry infinite | ||
| + | nobind | ||
| + | persist-key | ||
| + | persist-tun | ||
| + | ca ca.crt | ||
| + | comp-lzo | ||
| + | verb 4 | ||
| + | auth-user-pass | ||
| + | auth-nocache | ||
| + | </pre> | ||
| + | * Add the following to route all ipv4 traffic (with dns) throught the VPN (ipv6 not supported...??) | ||
| + | redirect-gateway def1 | ||
| + | * /!\ The certificate ca.crt must be in the same directory as foo.cfg, or change path in foo.cfg /!\ | ||
| + | * Then connect to the VPN | ||
| + | <pre> | ||
| + | $ openvpn foo.cfg | ||
| + | </pre> | ||
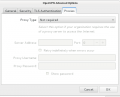
| − | + | === Gnome Network manager === | |
| − | + | <gallery> | |
| − | + | File:Screenshot_from_2013-01-02_00-51-24.png | |
| − | + | File:Screenshot_from_2013-01-02_00-51-51.png | |
| − | + | File:Screenshot_from_2013-01-02_00-52-14.png | |
| − | + | File:Screenshot_from_2013-01-02_00-52-31.png | |
| − | = | + | File:Screenshot_from_2013-01-02_00-52-48.png |
| − | + | </gallery> | |
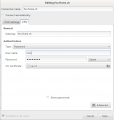
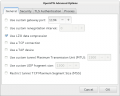
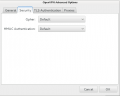
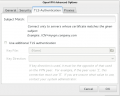
| − | == Gnome Network manager == | + | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
Latest revision as of 21:06, 27 December 2013
Information
- Easy access to the FIXME Network from the outside world
- This is part of the Internal_Server
- You must have a local account on foo and be in the vpnusers unix group
Client configuration
Command Line
- Copy this to ca.crt
-----BEGIN CERTIFICATE----- MIIDvDCCAyWgAwIBAgIJALowX2zad5mbMA0GCSqGSIb3DQEBBQUAMIGbMQswCQYD VQQGEwJDSDELMAkGA1UECBMCVkQxETAPBgNVBAcTCExhdXNhbm5lMRowGAYDVQQK ExFGSVhNRSBIQUNLRVJTUEFDRTEMMAoGA1UECxMDVlBOMRUwEwYDVQQDEwxmb28u Zml4bWUuY2gxDjAMBgNVBCkTBUZJWE1FMRswGQYJKoZIhvcNAQkBFgx2cG5AZml4 bWUuY2gwHhcNMTIxMjI4MjMzODE4WhcNMjIxMjI2MjMzODE4WjCBmzELMAkGA1UE BhMCQ0gxCzAJBgNVBAgTAlZEMREwDwYDVQQHEwhMYXVzYW5uZTEaMBgGA1UEChMR RklYTUUgSEFDS0VSU1BBQ0UxDDAKBgNVBAsTA1ZQTjEVMBMGA1UEAxMMZm9vLmZp eG1lLmNoMQ4wDAYDVQQpEwVGSVhNRTEbMBkGCSqGSIb3DQEJARYMdnBuQGZpeG1l LmNoMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDpL2ZXBJw9MX7b2iezP+P7 +hI4XjXx1HCyV1TmM2sXCxenN+BmS9uD+hz/kOtHxakVHsm4QKkqcppNJGscpZis HopK733rEviVARZxhn4ANEOp9JXeXu8hsy0hC5DEozGceSOzkxnJWUM64e7rhBzQ CiZN7FDrJN2ok1ifFEojtQIDAQABo4IBBDCCAQAwHQYDVR0OBBYEFJV7oFA/wZX1 Yp6enu/++UkotcrXMIHQBgNVHSMEgcgwgcWAFJV7oFA/wZX1Yp6enu/++UkotcrX oYGhpIGeMIGbMQswCQYDVQQGEwJDSDELMAkGA1UECBMCVkQxETAPBgNVBAcTCExh dXNhbm5lMRowGAYDVQQKExFGSVhNRSBIQUNLRVJTUEFDRTEMMAoGA1UECxMDVlBO MRUwEwYDVQQDEwxmb28uZml4bWUuY2gxDjAMBgNVBCkTBUZJWE1FMRswGQYJKoZI hvcNAQkBFgx2cG5AZml4bWUuY2iCCQC6MF9s2neZmzAMBgNVHRMEBTADAQH/MA0G CSqGSIb3DQEBBQUAA4GBAAi2XgH93CxEhff2Q5tk/B2hzu+xtcBLzYjcgq1QqJ63 ipG9maoav2UrjuWDjb+7WnzSe7JMF8Ay8CqWHgf9Dfqb04PLcIGPe5OPo8jlf4QF k1uBZs0F+Z2v1yq4EK4KJ/hJxLJIX6xs5UGeK2GaaHKROuQX9N5iIb6BhyA5tlzd -----END CERTIFICATE-----
- Put the following content in a foo.cfg configuration file
client dev tun proto udp remote foo.fixme.ch 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt comp-lzo verb 4 auth-user-pass auth-nocache
- Add the following to route all ipv4 traffic (with dns) throught the VPN (ipv6 not supported...??)
redirect-gateway def1
- /!\ The certificate ca.crt must be in the same directory as foo.cfg, or change path in foo.cfg /!\
- Then connect to the VPN
$ openvpn foo.cfg